How To Use Wireshark To Find Broadcast Storm

Suppose i m using wireshark to monitor a broadcast storm.
How to use wireshark to find broadcast storm. Capture for a minute or two and then stop. Layer 2 broadcast packets have the destination mac address as ff ff ff. Sort by number of packets. Talk to your isp they may hopefully know more the disabled you for a reason find out why. And finally use nslookup on the ip.
This tutorial understands how you can find broadcast storms using wireshark. It won t take long to get what you need during a storm. You could sniff them out. It won t take long to get what you need during a storm. How do i monitor this and obtain the exact time moment when wireshark capture buffer runs out of memory.
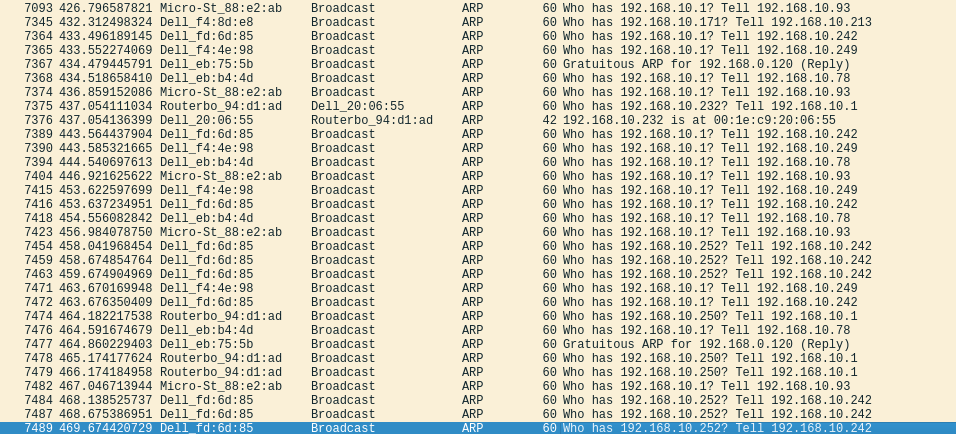
Get some wireshark dumps and i ll take a look. Detecting broadcast storm on a flat network as has been suggested you need to plug in a laptop into the network running a packet sniffer if you don t know exactly where the flood is coming from you may need to try it in several locations or have a few people help you out and sniff multiple sites at once. In wireshark go to statistics conversations ethernet and sort by the number of packets. Plug your laptop into the same vlan that is having the storm. So in wireshark you can apply a display filter eth dst ff ff ff ff ff ff and look at the frames which remain.
The unix janitor feb 9 12 at 16 04. To do this in the wireshark gui enter this into your filter and click apply. I want to find out the exact instant of time when the capture buffer runs out of memory. Capture for a minute or two and then stop. Icmpv6 broadcast storm wireshark network diagnostics wireshark netowrk diagnostics icmpv6 broadcast storm when i got back to work after the wonderful xmas break i made a start on installing 50 new desktop computers so i fired up my imaging system mdt wds and imaged all of the computers no problems.
If they all have the same source mac address it can be the source of the broadcast storms but it is not very likely. There are two types of broadcast which are layer 2 broadcast and layer 3 broadcast. When tracking down multicast and broadcast sources it is useful to be able to filter everything to leave only the multicast and broadcast traffic. You could sniff them out. There is your culprit in the top slot.